Deliver Secure Access to Azure Key Vault from AKS Powered by Tanzu

Overview
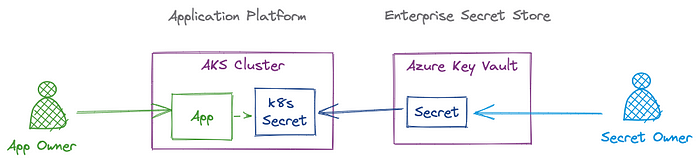
I’ve been in engaged in several discussions recently related to secrets management for Kubernetes. Particularly in use cases for applications that require credentials to access downstream services (e.g. databases). Sure, Kubernetes has the Secret resource. And for many small or bespoke implementations this may be the initial and perhaps final solution. However, it is common for enterprises to use an Enterprise Secret Store for credentials. And an enterprise may have 100s of k8s clusters. It can be overly burdensome for the credential owners to have to put the credentials in secrets in the right clusters, and maintain those secrets over time.
Continue reading this post at my Dodd Pfeffer Medium Blog where it was originally published.
